6
• Send LDAP ‘Start TLS’ Request – Some LDAP server implementations support the Start TLS
directive rather than using native LDAP over TLS. This allows the LDAP server to listen on one port
(normally 389) for LDAP connections, and to switch to TLS as directed by the client. Active Directory
does not use this option, and it should only be selected if required by your LDAP server.
• Require valid certificate from server – Validates the certificate presented by the server during the
TLS exchange, matching the name specified above to the name on the certificate. Deselecting this
default option will present an alert, but exchanges between the SonicWALL and the LDAP server will
still use TLS – only without issuance validation.
• Local certificate for TLS – Optional, to be used only if the LDAP server requires a client certificate
for connections. Useful for LDAP server implementations that return passwords to ensure the identity
of the LDAP client (Active Directory does not return passwords). This setting is not required for Active
Directory.
If your network uses multiple LDAP/AD servers with referrals, then select one as the primary server
(probably the one that holds the bulk of the users), and use the above settings for that server. It will then
refer the SonicWALL on to the other servers for users in domains other than its own. For the SonicWALL
to be able to log in to those other servers, each server must have a user configured with the same
credentials (user name, password and location in the directory) as the login to the primary server. This
may entail creating a special user in the directory for the SonicWALL login. Note that only read access to
the directory is required.
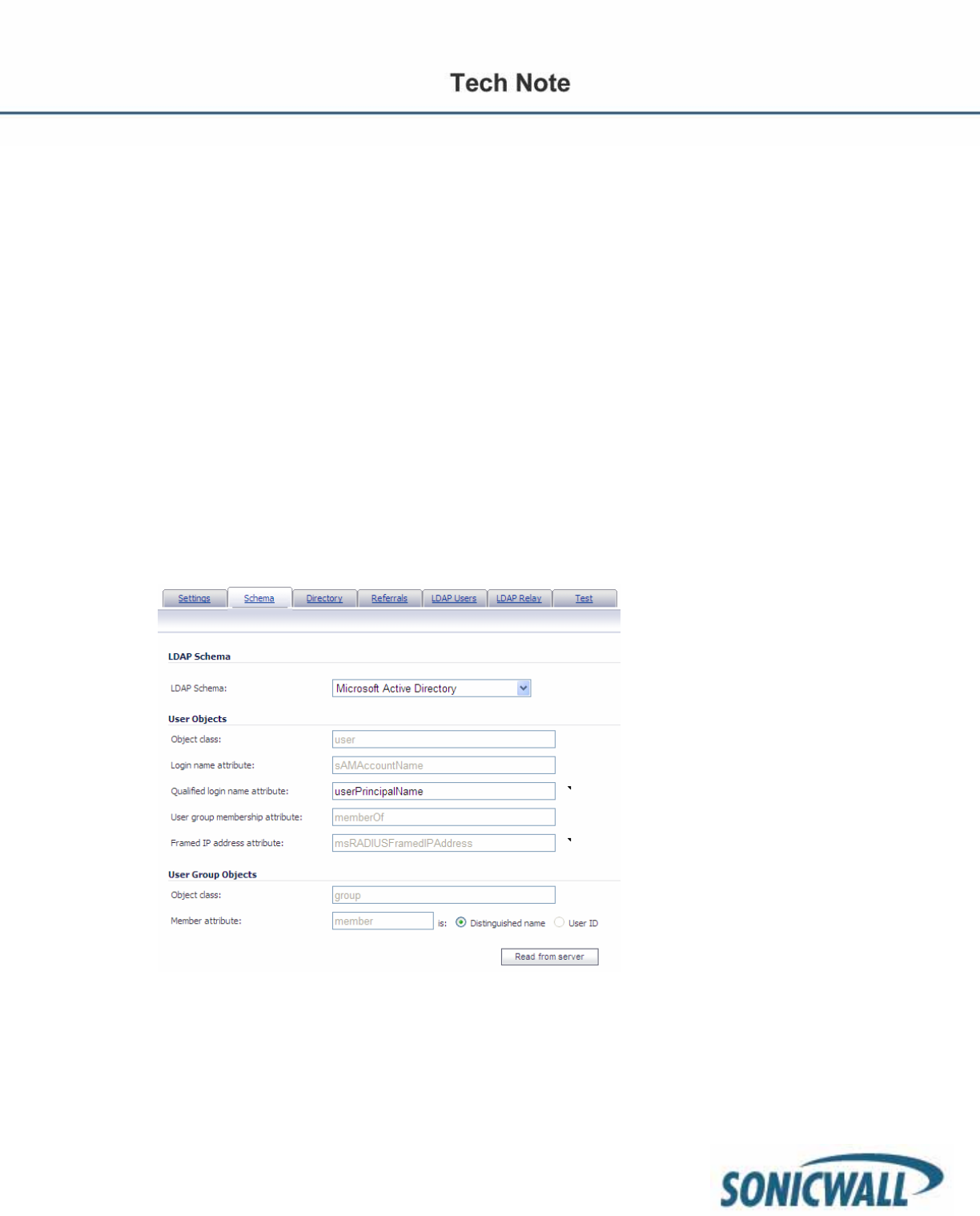
Step 6 On the Schema tab, configure the following fields:
• LDAP Schema – Select one of the following:
– Microsoft Active Directory
– RFC2798 inetOrgPerson
– RFC2307 Network Information Service
– Samba SMB
– Novell eDirectory
– User defined


















