Security Triggers 75
Models 2603, 2621, and 2635 Getting Started Guide 7 • Security
This example continues to allow pings over the firewall:
1. From the Configuration Menu, > Configuration > Security > Security Policy Configuration... > Port Filters...
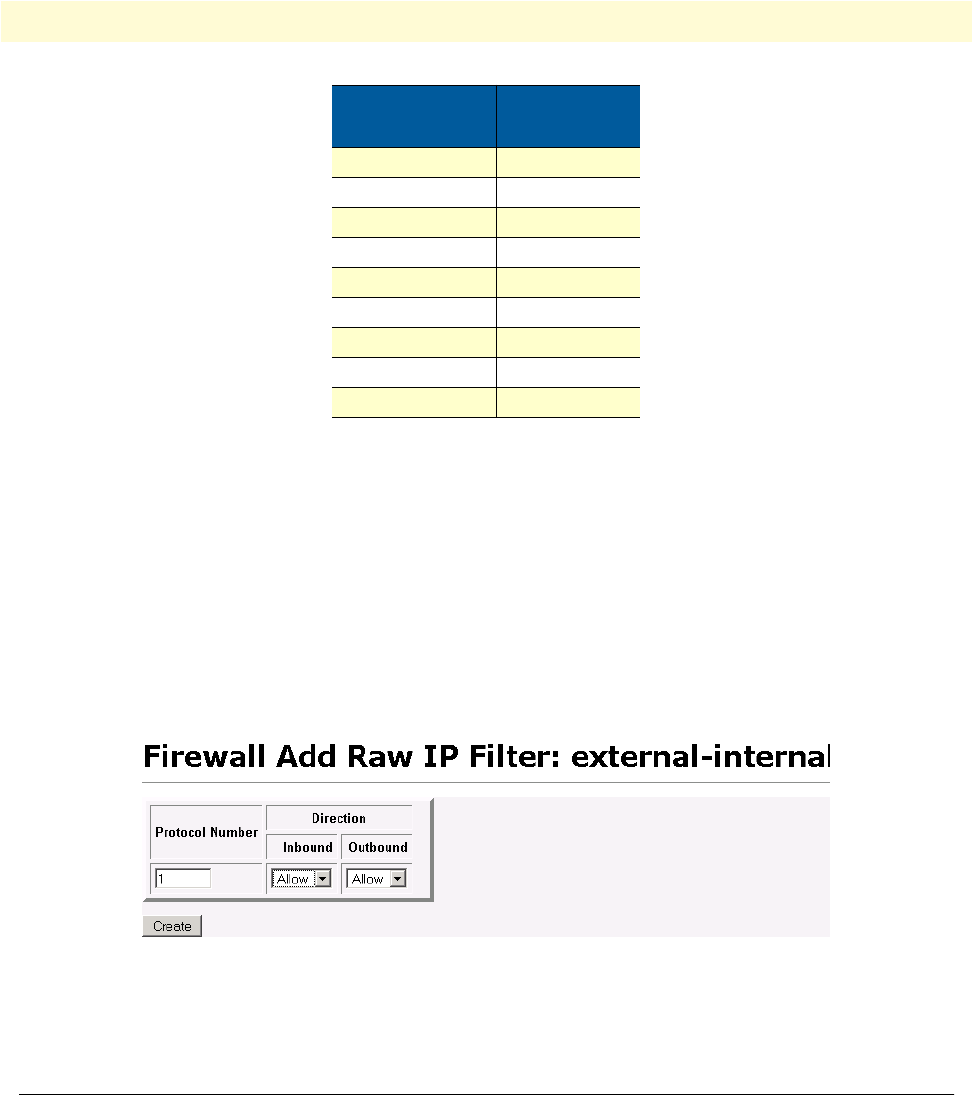
> Add Raw IP Filter
2. Enter 1 (for ICMP) in the Protocol Number field.
3. Set both Inbound and Outbound for Allow. (See figure 50.)
4. Click on Create.
Figure 50. Defining ICMP port filter for ping
You can now ping between the two networks
Security Triggers
Security triggers are used to allow an application to open a secondary port in order to transport data. The most
common example is FTP. This procedure sets up a trigger on the Firewall to permit an FTP session from PC A
to PC B, but not the reverse.
1. First, create an outbound-only portfilter for FTP and add it to the item0 policy.
2. Following the path given in step 1 for the ping portfilter in the previous section, click on Add TCP Filter.
3. The Port Range is entered as 21 for both Start and End.
6 TCP
8 EGP
9 IGP
17 UDP
46 RSVP
47 GRE
89 OSPFIGP
92 MTP
94 IPIP
Protocol
Number
Abbreviation


















