18
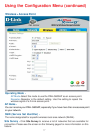
Channel - Select the channel from the pulldown menu. All devices on the network must
share the same channel to communicate.
Authentication -
Open System -
Shared Key -
Communicates the key across the network.
Hexadecimal digits consist of the numbers 0-9 and the letters A-F
ASCII (American Standard Code for Information Interchange) is a code for
representing English letters as numbers from 0-127
Using the Configuration Menu (continued)
Wireless > Access Point (continued)
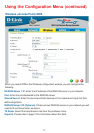
Devices must have identical WEP settings to communicate.
WPA -
TX Rates -
Select the transmission rate for the network.
WEP - Select Enable Encryption to use WEP (Wired Equivalent Privacy) on the
network. All devices on the network, including the access point, must share the same
WEP selection - either Enable or Disable.
WEP Encryption - Select either 64- or 128-bit length.
WEP Mode - Select ASCII or Hexadecimal mode and then input the appropriate
digits or letters into each Key field. You can create up to 4 keys. Select the key you
wish to use.
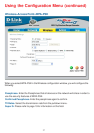
WPA-PSK-
For home users that will not incorporate a RADIUS server in
their network, the security for the DWL-G800AP, used in
conjunction with other WPA-compatible 802.11 products, will still
be much stronger than ever before. Utilizing the Pre-Shared
Key mode of WPA, the DWL-G800AP will obtain a new security
key every time it connects to the 802.11 network. You only need
to input your encryption information once in the configuration
menu. No longer will you have to manually input a new WEP key
frequently to ensure security. With the DWL-G800AP, you will
automatically receive a new key every time you connect, vastly
increasing the safety of your communication.
Wi-Fi Protected Access which authorizes and identifies users
based on a secret key that changes automatically at regular
intervals. WPA uses TKIP (Temporal Key Integrity Protocol)
to change the temporal key every 10,000 packets (a packet is a
kind of message transmitted over a network.) This ensures much
greater security than the standard WEP security. (By contrast,
the previous WEP encryption implementations required the keys
to be changed manually.)