ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Manually Configuring Internet and WAN Settings 3-15
v1.0, September 2009
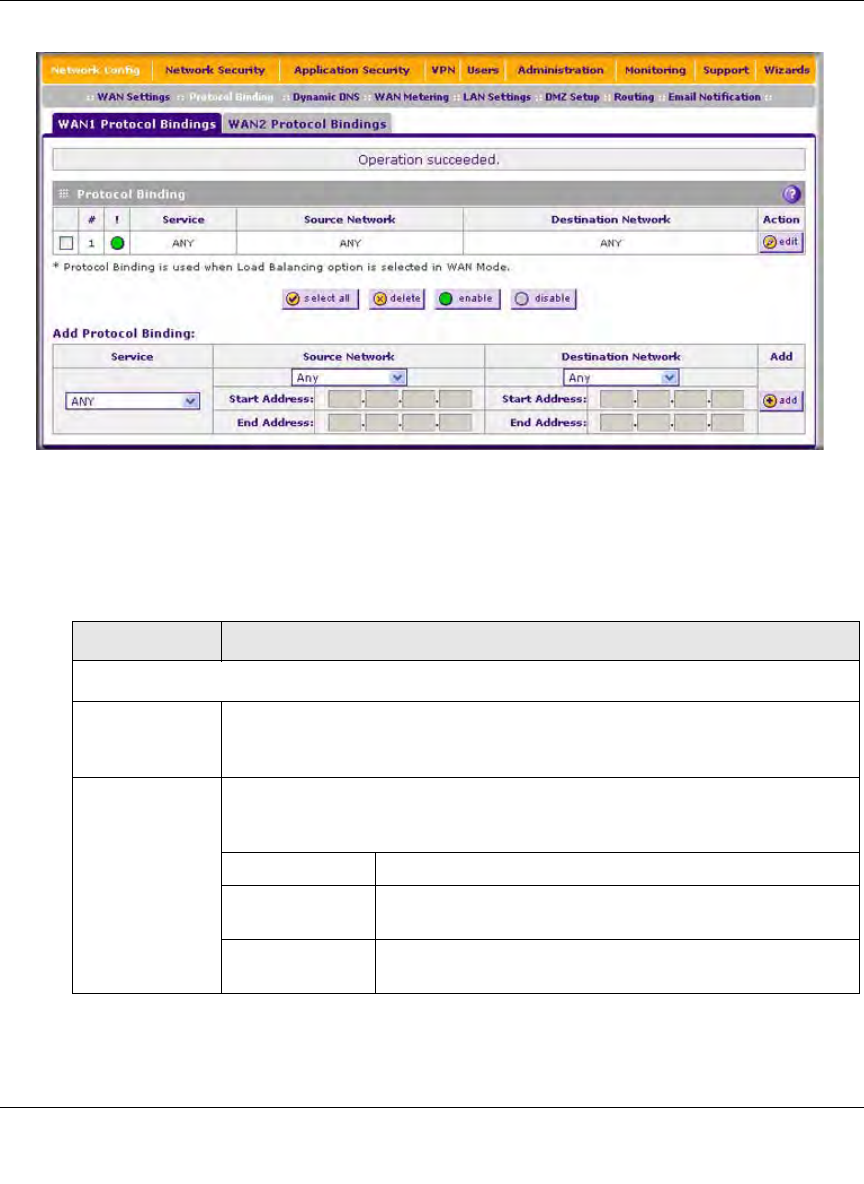
a. Figure 3-9 shows one example in the Protocol Binding table. Configure the protocol
binding settings as explained in Table 3-6.
Figure 3-9
Table 3-6. Protocol Binding Settings (UTM25 Only)
Setting Description (or Subfield and Description)
Add Protocol Binding
Service From the pull-down menu, select a service or application to be covered by this
rule. If the service or application does not appear in the list, you must define it
using the Services menu (see “Services-Based Rules” on page 5-3).
Source Network The source network settings determine which computers on your network are
affected by this rule. Select one of the following options from the pull-down
menu:
Any All devices on your LAN.
Single address In the Start Address field, enter the IP address to which the
rule is applied.
Address range In the Start Address field and End Address field, enter the
IP addresses for the range to which the rule is applied.


















