ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Firewall Protection 5-41
v1.0, September 2009
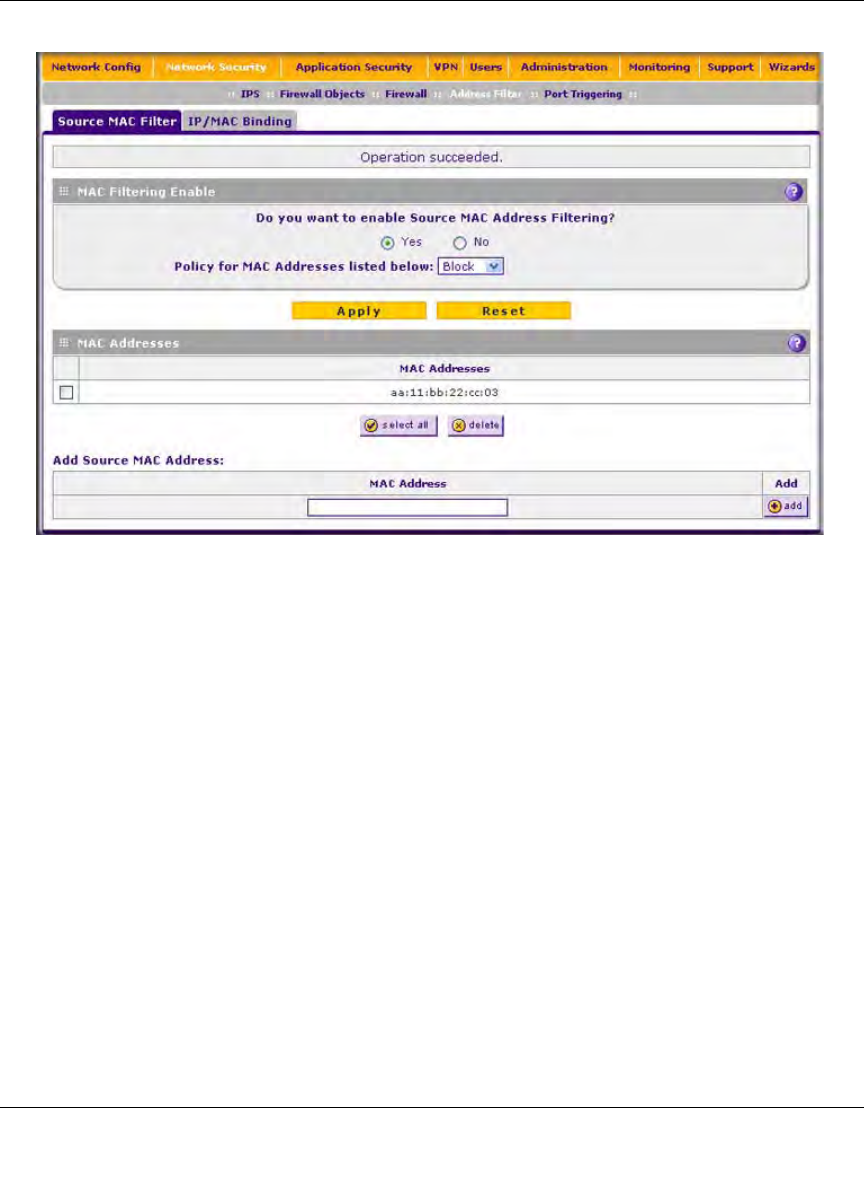
2. In the MAC Filtering Enable section, select the Yes radio button.
3. In the same section, select one of the following options from the pull-down menu (next to
Policy for MAC Addresses listed below):
• Block. Traffic coming from all addresses in the MAC Addresses table is blocked.
• Permit. Traffic coming from all addresses in the MAC Addresses table is permitted.
4. Below Add Source MAC Address, build your list of source MAC addresses to be permitted or
blocked by entering the first MAC address in the MAC Address field. A MAC address must be
entered in the form xx:xx:xx:xx:xx:xx, where x is a numeric (0 to 9) or a letter between and a
and f (inclusive), for example: aa:11:bb:22:cc:03.
5. Click the add table button. The MAC address is added to the MAC Addresses table.
6. Click Apply to save your settings.
To remove one or more entries from the table:
1. Select the checkbox to the left of the MAC address that you want to delete or click the select
all table button to select all entries.
2. Click the delete table button.
Figure 5-26


















