ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
6-38 Content Filtering and Optimizing Scans
v1.0, September 2009
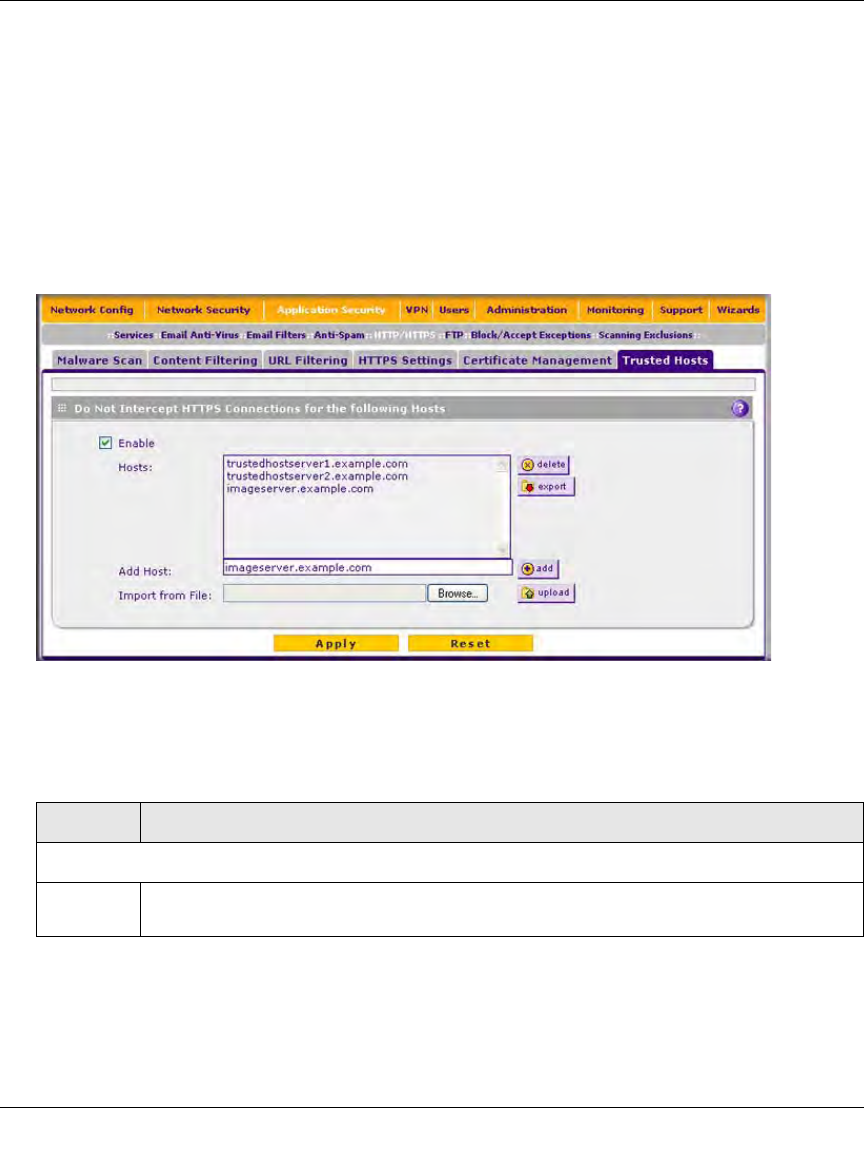
To completely bypass the scanning of the https://example.com site, you must add all three hosts to
the trusted hosts list because different files from these three hosts are also downloaded when a user
attempts to access the https://example.com site.
To specify trusted hosts:
1. Select Application Security > HTTP/HTTPS from the menu. The HTTP/HTTPS submenu
tabs appear, with the Malware Scan screen in view.
2. Click the Trusted Hosts submenu tab. The Trusted Hosts screen displays. (Figure 6-16 shows
some examples.)
3. Enter the settings as explained in Table 6-11.
Figure 6-16
Table 6-11. Trusted Hosts Settings
Setting Description (or Subfield and Description)
Do Not Intercept HTTPS Connections for the following Hosts
Enable Select this checkbox to bypass scanning of trusted hosts that are listed in the Hosts field.
Users do not receive a security alert for trusted hosts that are listed in the Host field.


















