Chapter 6 Device Security Settings
Vantage CNM User’s Guide
117
6.1.2 Rule Summary
Use the Insert button to add a new rule before an existing rule. Use Move to put an existing
rule in a different place.
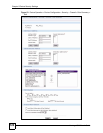
Select a device, click Device Operation in the menu bar and then click Device Configuration
> Security > Firewall > Rule Summary in the navigation panel.
From, To Set the firewall’s default actions based on the direction of travel of
packets. Here are some example descriptions of the directions of
travel.
From LAN To LAN means packets traveling from a computer on one
LAN subnet to a computer on another LAN subnet on the LAN interface
of the device or the device itself. The device does not apply the firewall
to packets traveling from a LAN computer to another LAN computer on
the same subnet.
From VPN means traffic that came into the device through a VPN
tunnel and is going to the selected “to” interface. For example, From
VPN To LAN specifies the VPN traffic that is going to the LAN. The
device applies the firewall to the traffic after decrypting it.
To VPN is traffic that comes in through the selected “from” interface
and goes out through any VPN tunnel. For example, From LAN To
VPN specifies the traffic that is coming from the LAN and going out
through a VPN tunnel. The device applies the firewall to the traffic
before encrypting it.
From VPN To VPN means traffic that comes in through a VPN tunnel
and goes out through (another) VPN tunnel or terminates at the device.
This is the case when the device is the hub in a hub-and-spoke VPN.
This is also the case if you allow someone to use a service (like Telnet
or HTTP) through a VPN tunnel to manage the device. The device
applies the firewall to the traffic after decrypting it.
Note: The VPN connection directions apply to the traffic
going to or from the device’s VPN tunnels. They do
not apply to other VPN traffic for which the device is
not one of the gateways (VPN pass-through traffic).
Here are the default actions from which you can select.
Select Drop to silently discard the packets without sending a TCP reset
packet or an ICMP destination-unreachable message to the sender.
Select Reject to deny the packets and send a TCP reset packet (for a
TCP packet) or an ICMP destination-unreachable message (for a UDP
packet) to the sender.
Select Permit to allow the passage of the packets.
The firewall rules for the WAN port with a higher route priority also
apply to the dial backup connection.
Log Select the check box next to a direction of packet travel to create a log
when the above action is taken for packets that are traveling in that
direction and do not match any of your customized rules.
Apply Click Apply to save your changes back to the device.
Reset Click this to reset this screen to its last saved values.
Table 42 Device Operation > Device Configuration > Security > Firewall > Default Rule
LABEL DESCRIPTION