Chapter 6 Device Security Settings
Vantage CNM User’s Guide
123
The following table describes the labels in this screen.
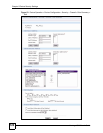
6.1.5 Threshold
Click Device Operation in the menu bar and then click Device Configuration > Security >
Firewall > Threshold in the navigation panel to bring up the next screen. The global values
specified for the threshold and timeout apply to all TCP connections.
Figure 55 Device Operation > Device Configuration > Security > Firewall > Threshold
Table 45 Device Operation > Device Configuration > Security > Firewall > Anti-Probing
LABEL DESCRIPTION
Respond to PING
on
Select the interfaces on which you want the device to reply to incoming Ping
requests.
Do not respond to
requests for
unauthorized
services.
Select this option to prevent hackers from finding the device by probing for unused
ports. If you select this option, the device will not respond to port request(s) for
unused ports, thus leaving the unused ports and the device unseen. If this option
is not selected, the device will reply with an ICMP port unreachable packet for a
port probe on its unused UDP ports and a TCP reset packet for a port probe on its
unused TCP ports.
Note that the probing packets must first traverse the device's firewall rule checks
before reaching this anti-probing mechanism. Therefore if a firewall rule stops a
probing packet, the device reacts based on the firewall rule to either send a TCP
reset packet for a blocked TCP packet (or an ICMP port-unreachable packet for a
blocked UDP packets) or just drop the packets without sending a response packet.
Apply Click Apply to save your changes back to the device.
Reset Click Reset to begin configuring this screen afresh.