Chapter 6 Device Security Settings
Vantage CNM User’s Guide
139
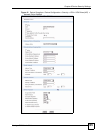
6.3.4 Move an IKE Network Policy
In the VPN Rule (IKE) screen, click the move icon to display the screen shown next.Use this
screen to associate a network policy to a gateway policy.
SA Life Time
(Seconds)
Define the length of time before an IPSec SA automatically renegotiates in this
field. The minimum value is 180 seconds.
A short SA Life Time increases security by forcing the two VPN gateways to
update the encryption and authentication keys. However, every time the VPN
tunnel renegotiates, all users accessing remote resources are temporarily
disconnected.
Perfect Forward
Secret (PFS)
Select whether or not you want to enable Perfect Forward Secrecy (PFS) and, if
you do, which Diffie-Hellman key group to use for encryption. Choices are:
NONE - disable PFS
DH1 - enable PFS and use a 768-bit random number
DH2 - enable PFS and use a 1024-bit random number
DH5 - enable PFS and use a 1536-bit random number
PFS changes the root key that is used to generate encryption keys for each
IPSec SA. The longer the key, the more secure the encryption, but also the
longer it takes to encrypt and decrypt information. Both routers must use the
same DH key group.
Enable Replay
Detection
As a VPN setup is processing intensive, the system is vulnerable to Denial of
Service (DOS) attacks. The IPSec receiver can detect and reject old or
duplicate packets to protect against replay attacks. Enable replay detection by
selecting this check box.
Enable Multiple
Proposals
Select this check box to allow the device to use any of its phase 1 or phase 2
encryption and authentication algorithms when negotiating an IPSec SA.
When you enable multiple proposals, the device allows the remote IPSec router
to select which encryption and authentication algorithms to use for the VPN
tunnel, even if they are less secure than the ones you configure for the VPN
rule.
Clear this check box to have the device use only the phase 1 or phase 2
encryption and authentication algorithms configured below when negotiating an
IPSec SA.
Apply Click Apply to save the changes.
Cancel Click Cancel to discard all changes and return to the main VPN screen.
Table 51 Device Operation > Device Configuration > Security > VPN > VPN Rules (IKE) >
Network Policy Add/Edit (continued)
LABEL DESCRIPTION