Chapter 6 Device Security Settings
Vantage CNM User’s Guide
136
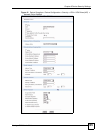
The following table describes the labels in this screen.
Table 51 Device Operation > Device Configuration > Security > VPN > VPN Rules (IKE) >
Network Policy Add/Edit
LABEL DESCRIPTION
Active If the Active check box is selected, packets for the tunnel trigger the device to
build the tunnel.
Clear the Active check box to turn the network policy off. The device does not
apply the policy. Packets for the tunnel do not trigger the tunnel.
If you clear the Active check box while the tunnel is up (and click Apply), you
turn off the network policy and the tunnel goes down.
Name Type a name to identify this VPN network policy. You may use any character,
including spaces, but the device drops trailing spaces.
Protocol Enter 1 for ICMP, 6 for TCP, 17 for UDP, etc. 0 is the default and signifies any
protocol.
Nailed-Up Select this check box to turn on the nailed up feature for this SA.
Turn on nailed up to have the device automatically reinitiate the SA after the SA
lifetime times out, even if there is no traffic. The device also reinitiates the SA
when it restarts.
The device also rebuilds the tunnel if it was disconnected due to the output or
input idle timer.
Allow NetBIOS
Traffic Through
IPSec Tunnel
NetBIOS (Network Basic Input/Output System) are TCP or UDP packets that
enable a computer to connect to and communicate with a LAN. It may
sometimes be necessary to allow NetBIOS packets to pass through VPN
tunnels in order to allow local computers to find computers on the remote
network and vice versa.
Select this check box to send NetBIOS packets through the VPN connection.
Check IPSec Tunnel
Connectivity
Select the check box and configure an IP address in the Ping this Address
field to have the device periodically test the VPN tunnel to the remote IPSec
router.
The device pings the IP address every minute. The device starts the IPSec
connection idle timeout timer when it sends the ping packet. If there is no traffic
from the remote IPSec router by the time the timeout period expires, the device
disconnects the VPN tunnel.
Log Select this check box to set the device to create logs when it cannot ping the
remote device.
Ping this Address If you select Check IPSec Tunnel Connectivity, enter the IP address of a
computer at the remote IPSec network. The computer's IP address must be in
this IP policy's remote range (see the Remote Network fields).
Gateway Policy
Information
Gateway Policy Select the gateway policy with which you want to use the VPN policy.
Virtual Address
Mapping Rule
Virtual address mapping over VPN is available with the routing and zero
configuration modes.
Active Enable this feature to have the device use virtual (translated) IP addresses for
the local network for the VPN connection. You do not configure the Local
Network fields when you enable virtual address mapping.
Virtual address mapping allows local and remote networks to have overlapping
IP addresses. Virtual address mapping (NAT over IPSec) translates the source
IP addresses of computers on your local network to other (virtual) IP addresses
before sending the packets to the remote IPSec router. This translation hides
the source IP addresses of computers in the local network.