Chapter 31 ADP
ZyWALL USG 50 User’s Guide
525
31.4 ADP Technical Reference
This section is divided into traffic anomaly background information and protocol
anomaly background information.
Traffic Anomaly Background Information
The following sections may help you configure the traffic anomaly profile screen
(Section 31.3.4 on page 518).
Port Scanning
An attacker scans device(s) to determine what types of network protocols or
services a device supports. One of the most common port scanning tools in use
today is Nmap.
Many connection attempts to different ports (services) may indicate a port scan.
These are some port scan types:
•TCP Portscan
•UDP Portscan
• IP Portscan
An IP port scan searches not only for TCP, UDP and ICMP protocols in use by the
remote computer, but also additional IP protocols such as EGP (Exterior Gateway
Protocol) or IGP (Interior Gateway Protocol). Determining these additional
protocols can help reveal if the destination device is a workstation, a printer, or a
router.
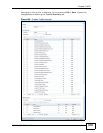
OK Click OK to save your settings to the ZyWALL, complete the profile and
return to the profile summary page.
Cancel Click Cancel to return to the profile summary page without saving any
changes.
Save Click Save to save the configuration to the ZyWALL but remain in the
same page. You may then go to the another profile screen (tab) in order
to complete the profile. Click OK in the final profile screen to complete the
profile.
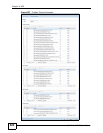
Table 157 Configuration > ADP > Profile > Protocol Anomaly (continued)
LABEL DESCRIPTION