Content Filtering and Optimizing Scans
229
ProSecure Unified Threat Management (UTM) Appliance
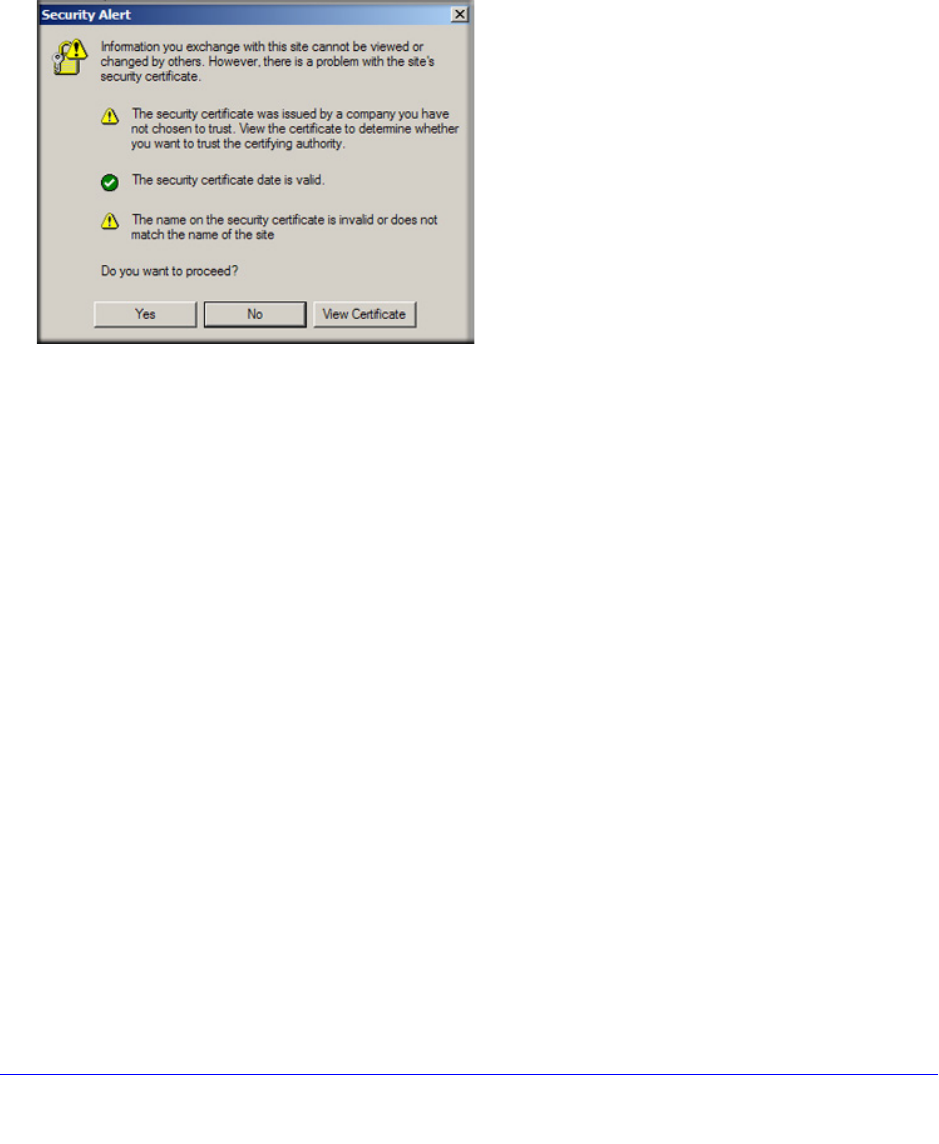
During SSL authentication, the HTTPS client authenticates three items:
• Is the SSL certificate trusted?
• Has the SSL certificate expired?
• Does the name on the SSL certificate match that of the website?
If one of these items is not authenticated, a security alert message displays in the browser
window:
Figure 124.
However, even when a certificate is trusted or still valid, or when the name of a certificate
does match the name of the website, a security alert message still displays when a user who
is connected to the UTM visits an HTTPS site. The appearance of this security alert message
is expected behavior because the HTTPS client receives a certificate from the UTM instead
of directly from the HTTPS server. If you want to prevent this security alert message from
displaying, install a root certificate on the client computer. The root certificate can be
downloaded from the UTM’s Manager Login screen (see Figure 20 on page 43).
If client authentication is required, the UTM might not be able to scan the HTTPS traffic
because of the nature of SSL. SSL has two parts—client and server authentication. HTTPS
server authentication occurs with every HTTPS request, but HTTPS client authentication is
not mandatory, and rarely occurs. Therefore it is of less importance whether the HTTPS
request comes from the UTM or from the real HTTPS client.
However, certain HTTPS servers do require HTTPS client certificate authentication for every
HTTPS request. Because of the design of SSL, the HTTPS client needs to present its own
certificate in this situation rather than using the one from the UTM, preventing the UTM from
scanning the HTTPS traffic. For information about certificates, see Manage SSL Certificates
for HTTPS Scanning on page 231.
You can specify trusted hosts for which the UTM bypasses HTTPS traffic scanning. For more
information, see Specify Trusted Hosts for HTTPS Scanning on page 235.


















