Virtual Private Networking Using IPSec, PPTP, or L2TP Connections
270
ProSecure Unified Threat Management (UTM) Appliance
Tip: To ensure that tunnels stay active, after completing the wizard, manually
edit the VPN policy to enable keep-alives, which periodically sends ping
packets to the host on the peer side of the network to keep the tunnel
alive. For more information, see Configure Keep-Alives on page 328.
Tip: For DHCP WAN configurations, first set up the tunnel with IP addresses.
After you have validated the connection, you can use the wizard to
create new policies using the FQDN for the WAN addresses.
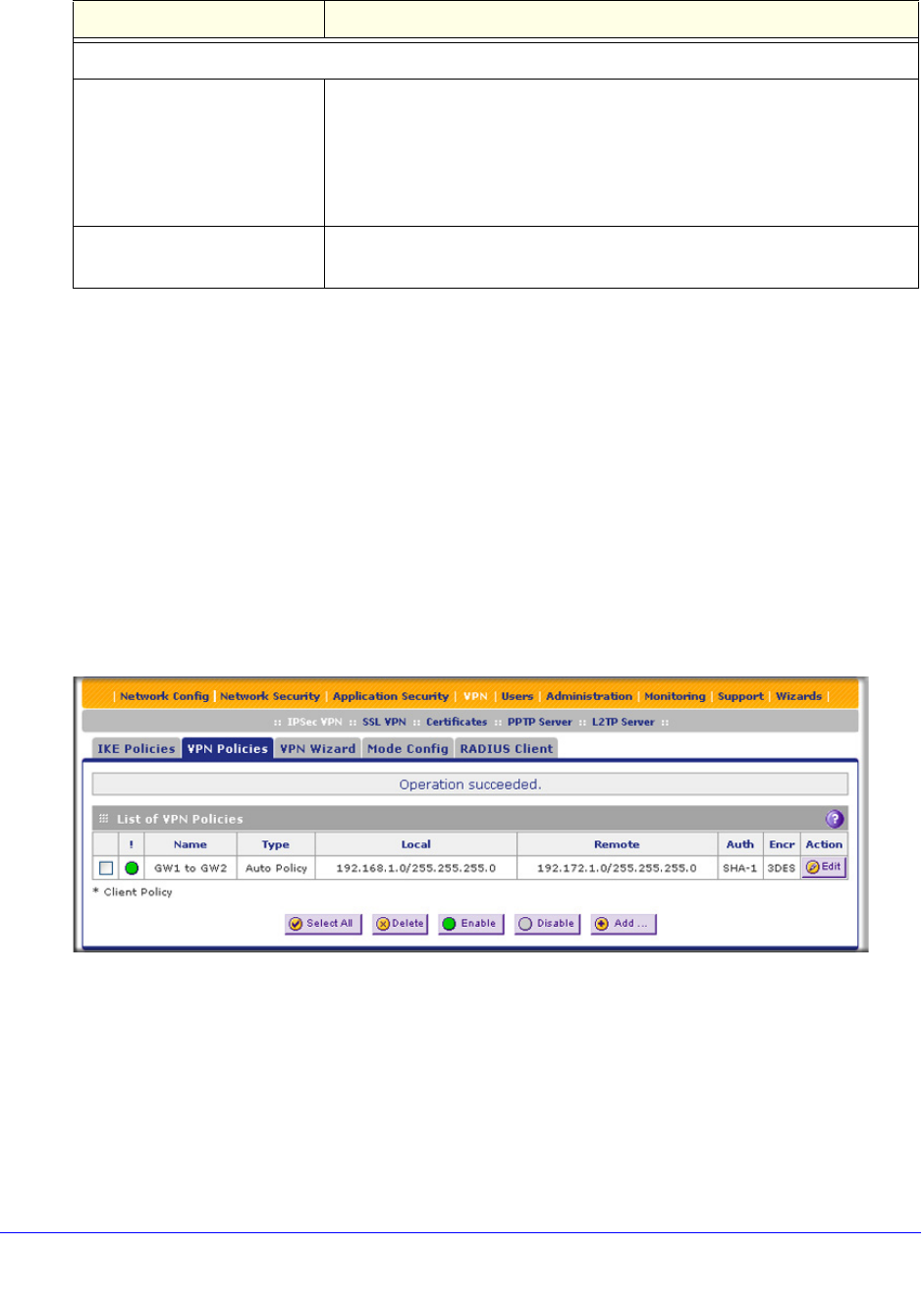
3. Click Apply to save your settings. The IPSec VPN policy is now added to the List of VPN
Policies table on the VPN Policies screen. By default, the VPN policy is enabled.
Figure 154.
4. Configure a VPN policy on the remote gateway that allows connection to the UTM.
5. Activate the IPSec VPN connection:
a. Select Monitoring > Active Users & VPNs > IPSec VPN Connection Status. The
IPSec VPN Connection Status screen displays.
Secure Connection Remote Accessibility
What is the remote LAN IP
Address?
Enter the LAN IP address of the remote gateway.
Note: The remote LAN IP address needs to be in a different subnet than
the local LAN IP address. For example, if the local subnet is 192.168.1.x,
then the remote subnet could be 192.168.10.x. but could not be
192.168.1.x. If this information is incorrect, the tunnel fails to connect.
What is the remote LAN
Subnet Mask?
Enter the LAN subnet mask of the remote gateway.
a. Both local and remote endpoints should be defined as either FQDNs or IP addresses. A combination of
an IP address and an FQDN is not supported.
Table 62. IPSec VPN Wizard settings for a gateway-to-gateway tunnel (continued)
Setting Description
