Wireless Network Module for the UTM9S and UTM25S
584
ProSecure Unified Threat Management (UTM) Appliance
• In infrastructure mode, wireless devices normally scan all channels, looking for a wireless
access point. If more than one wireless access point can be used, the one with the
strongest signal is used. This can happen only when the wireless access points use the
same SSID. The wireless network module functions in infrastructure mode by default.
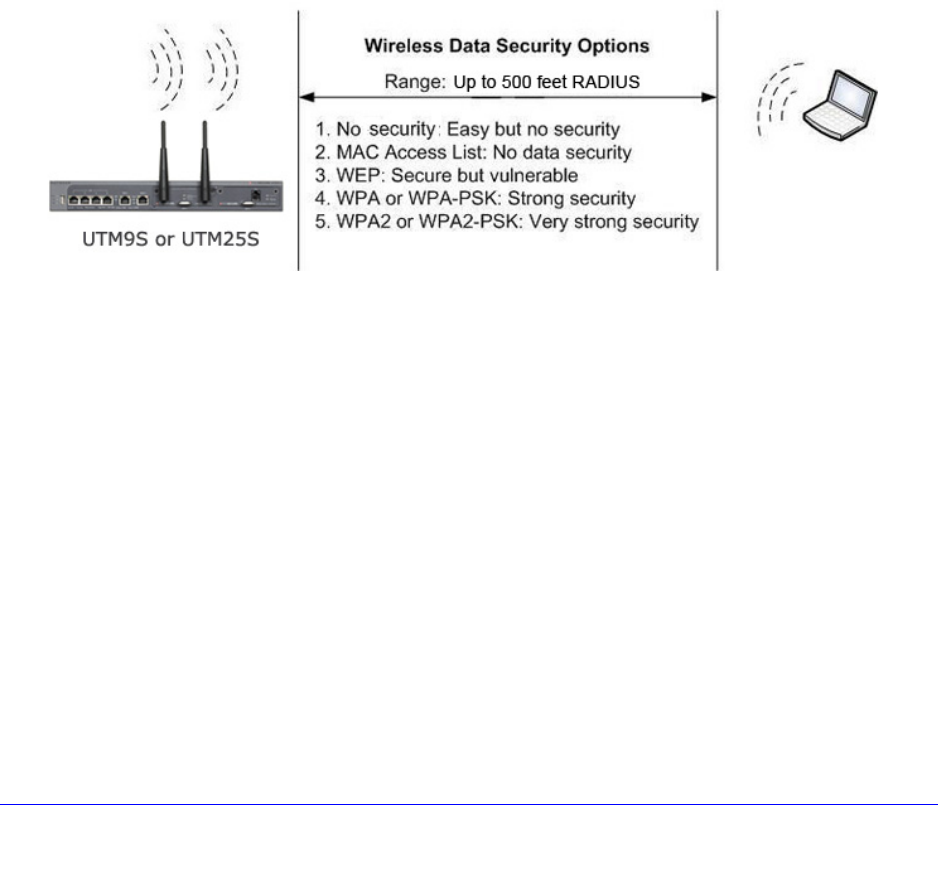
Wireless Data Security Options
Indoors, computers can connect over 802.11n wireless networks at a maximum range of
300 feet. Typically, a UTM9S or UTM25S inside a building works best with wireless devices
within a 100-foot radius. Such distances can allow for others outside your immediate area to
access your network.
Unlike wired network data, your wireless data transmissions can extend beyond your walls
and can be received by anyone with a compatible adapter. For this reason, use the security
features of your wireless equipment. The wireless network module provides highly effective
wireless security features that are covered in detail in this appendix. Deploy the security
features appropriate to your needs.
Figure 340.
There are several ways you can enhance the security of your wireless network:
• Restrict access based by MAC address. You can allow only trusted computers to
connect so that unknown computers cannot wirelessly connect to the wireless network
module. Restricting access by MAC address adds an obstacle against unwanted access
to your network, but the data broadcast over the wireless link is fully exposed. For
information about how to restrict access by MAC address, see Restrict Wireless Access
by MAC Address on page 593.
• Turn off the broadcast of the wireless network name (SSID). If you disable broadcast
of the SSID, only devices that have the correct SSID can connect. This nullifies the
wireless network discovery feature of some products, such as Windows XP, but the data
is still exposed. For information about how to turn of broadcast of the SSID, see
Configure and Enable Wireless Profiles on page 588.
• WEP. Wired Equivalent Privacy (WEP) data encryption provides data security. WEP
shared key authentication and WEP data encryption block all but the most determined
eavesdropper. This data encryption mode has been superseded by WPA-PSK and
WPA2-PSK.


















