Content Filtering and Optimizing Scans
234
ProSecure Unified Threat Management (UTM) Appliance
The Trusted Certificates table contains the trusted certificates from third-party websites that
are signed by the certification authorities. The UTM comes standard with trusted certificates
that are preloaded in the Trusted Certificates table.
To import a trusted certificate:
1. In the Import New Certificate section of the screen, click Browse next to the Import from
File field.
2. Navigate to a trusted certificate file on your computer. Follow the instructions of your
browser to place the certificate file in the Import from File field.
3. Click the Upload button. The newly imported trusted certificate is added to the Trusted
Certificates table.
To view details of a trusted certificate:
1. From the Trusted Certificates table, select the certificate.
2. Click View Details. A new screen opens that displays the details of the certificate.
To delete a trusted certificate:
1. From the Trusted Certificates table, select the certificate.
2. Click Delete Selected.
Manage Untrusted HTTPS Certificates
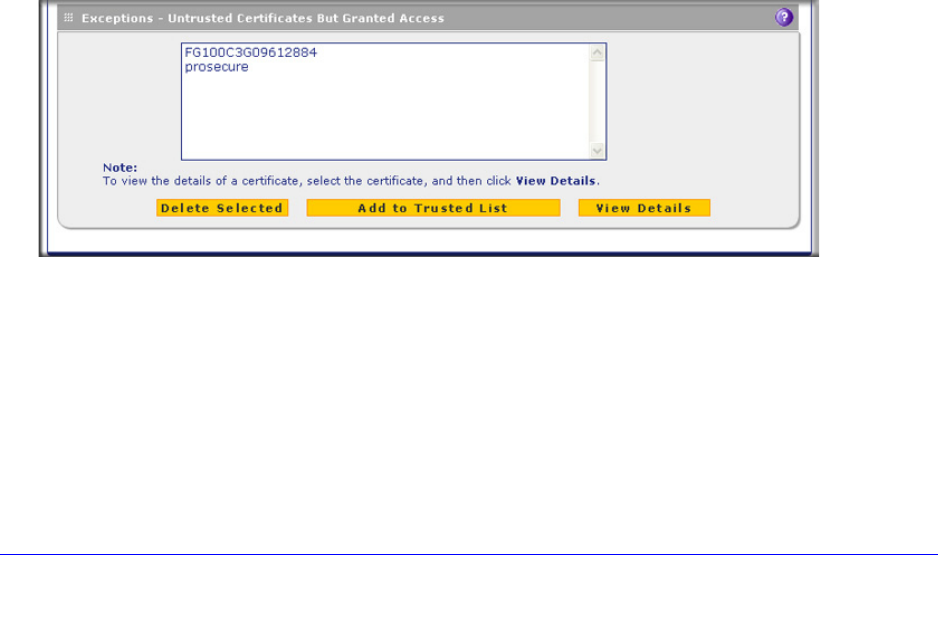
To manage untrusted certificates, select Web Security > Certificate Management. The
Certificate Management screen displays. The following figure shows only the Exceptions -
Untrusted Certificates But Granted Access section of the screen:
Figure 129. Certificate management, screen 3 of 3
When the UTM detects an untrusted or invalid certificate, it automatically places the
certificate in the Exceptions - Untrusted Certificates But Granted Access table.
To view details of an untrusted certificate:
1. From the Exceptions - Untrusted Certificates But Granted Access table, select the
certificate.
2. Click View Details. A new screen opens that displays the details of the certificate.


















