Network and System Management
442
ProSecure Unified Threat Management (UTM) Appliance
2. Enter the settings as explained in the following table:
3. Click Apply to save your settings.
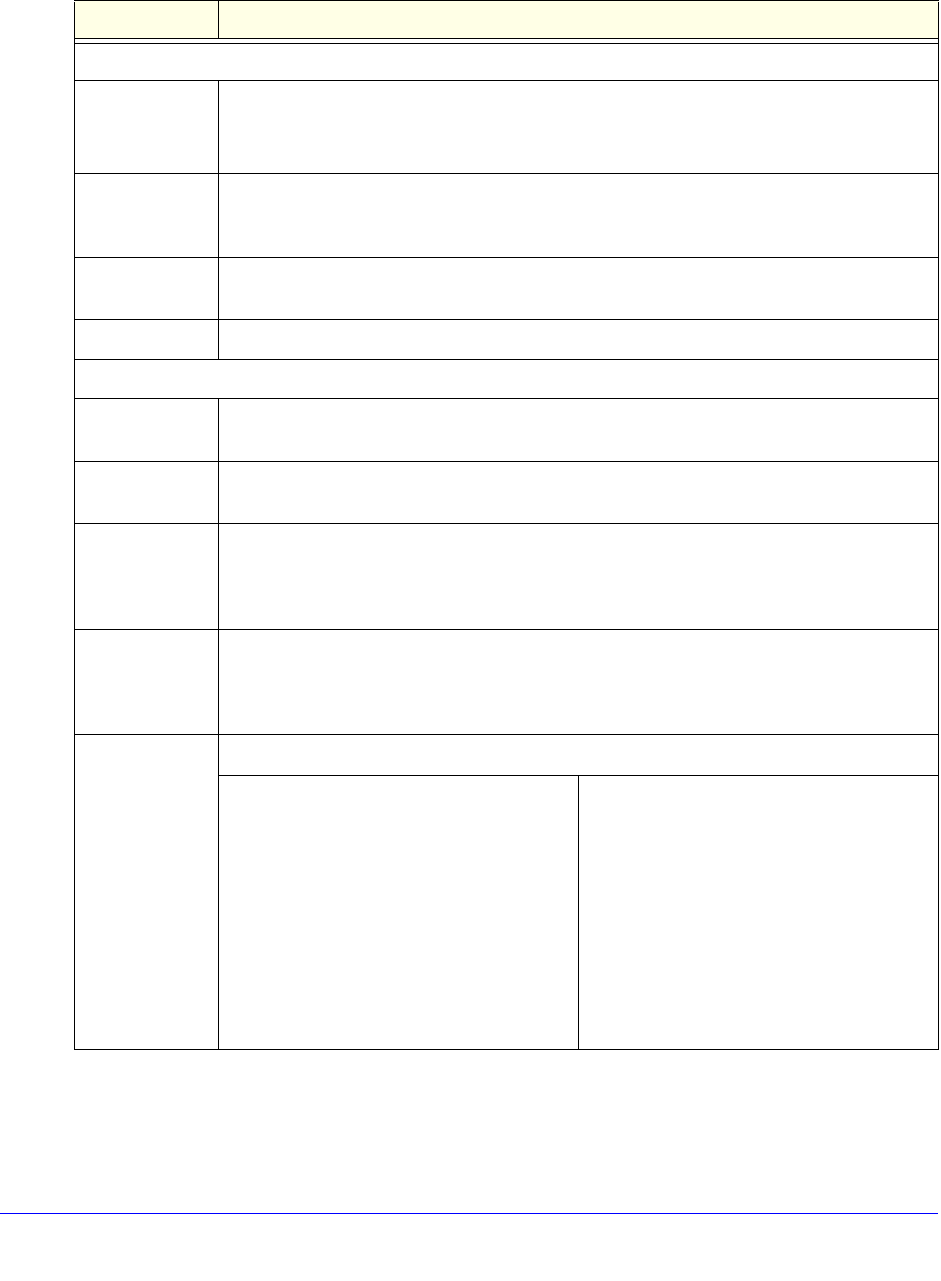
Table 108. Global SNMP settings and SNMPv1/v2c settings
Setting Description
SNMP Global Settings
Do You Want to
Enable SNMP?
Select one of the following radio buttons:
• Yes. Enable SNMP.
• No. Disable SNMP. This is the default setting.
Enable Access
From WAN
Select the Enable Access From WAN check box to allow SNMP management over a
WAN connection. This check box is cleared by default, allowing SNMP management only
over a LAN connection.
Contact The SNMP system contact information that is available to the SNMP manager. This
setting is optional.
Location The physical location of the UTM. This setting is optional.
SNMPv1/v2c Settings
Read
Community
The community string to allow an SNMP manager access to the MIB objects of the UTM
for reading only. The default setting is public.
Set Community The community string to allow an SNMP manager access to the MIB objects of the UTM
for reading and writing. The default setting is private.
Trusted SNMP
Hosts
Enter the IP addresses of the computers and devices to which you want to grant
read-only (GET) or write (SET) privileges on the UTM. Separate IP addresses by a
comma. To allow any trusted SNMP host access, leave the field blank, which is the
default setting.
SNMP Traps Enter the IP addresses of the SNMP management stations that are allowed to receive the
UTM’s SNMP traps. Separate IP addresses by a comma. If you leave the field blank,
which is the default setting, no SNMP management station can receive the UTM’s SNMP
traps.
Events Select the check boxes for the events for which SNMP traps should be sent:
• WAN connection failure
• Licenses status changed
• Service status changed
• Spam detected
• Malware detected
• Malware outbreak
• IPS detected
• IPS outbreak
• WAN failover detected
• User login failed
• Traffic occurred
• Component updated
• System status changed
• Dos attack detected
• Port scan attack detected
• Firewall event detected
• IPSec VPN detected
• SSL VPN detected
• User login detected


















