Monitor System Access and Performance
481
ProSecure Unified Threat Management (UTM) Appliance
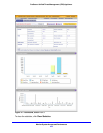
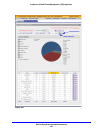
The following table explains the fields of the Most Recent 5 and Top 5 sections of the
Dashboard screen:
Table 120. Dashboard screen: most recent 5 threats and top 5 threats information
Category Most recent 5 threats description Top 5 threats description
Threats
• Malware Name. The name of the
malware threat.
• Protocol. The protocol in which the
malware threat was detected.
• Date and Time. The date and time that
the malware threat was detected.
• Malware Name. The name of the
malware threat.
• Count. The number of times that the
malware threat was detected.
• Percentage. The percentage that the
malware threat represents in relation to
the total number of detected malware
threats.
IPS Signatures • Signature Name. The name of the
attack.
• Category. The category in which the
attack was detected, such as Web,
Mail, Databases, and so on. (For more
information about categories, see
Enable and Configure the Intrusion
Prevention System on page 187.)
• Date and Time. The date and time that
the attack was detected.
• Signature Name. The name of the
attack.
• Count. The number of times that the
attack was detected.
• Percentage. The percentage that the
attack represents in relation to the total
number of detected attacks.
Applications • Application. The name of the
application that was blocked.
• Category. Instant messaging or
peer-to-peer.
• Date and Time. The date and time that
the application request was blocked.
• Application. The name of the
application that was blocked.
• Requests. The total number of user
requests for the blocked application.
• Source IPs. The source IP address
from which the request came.
Web Categories
• Category. The web category that was
blocked. (For more information about
web categories, see Configure Web
Content Filtering on page 218.)
• Date and Time. The date and time that
the web request was blocked.
• Category. The web category that was
blocked. (For more information about
web categories, see Con
figure Web
Content Filtering on page 218.)
• Requests. The total number of user
requests for the blocked web category.
• Source IPs. The source IP address
from which the request came.
Spam • Email Subject. The email subject line
in the spam message.
• Date and Time. The date and time that
the spam message was detected.
• Recipient. The intended recipient of the
spam message.
• Emails. The number of spam
messages for the intended recipient.