Monitor System Access and Performance
516
ProSecure Unified Threat Management (UTM) Appliance
2. Enter the settings as explained in the following table:
3. Click Search. The log is queried according to the search criteria that you specified, and the
search results are displayed onscreen.
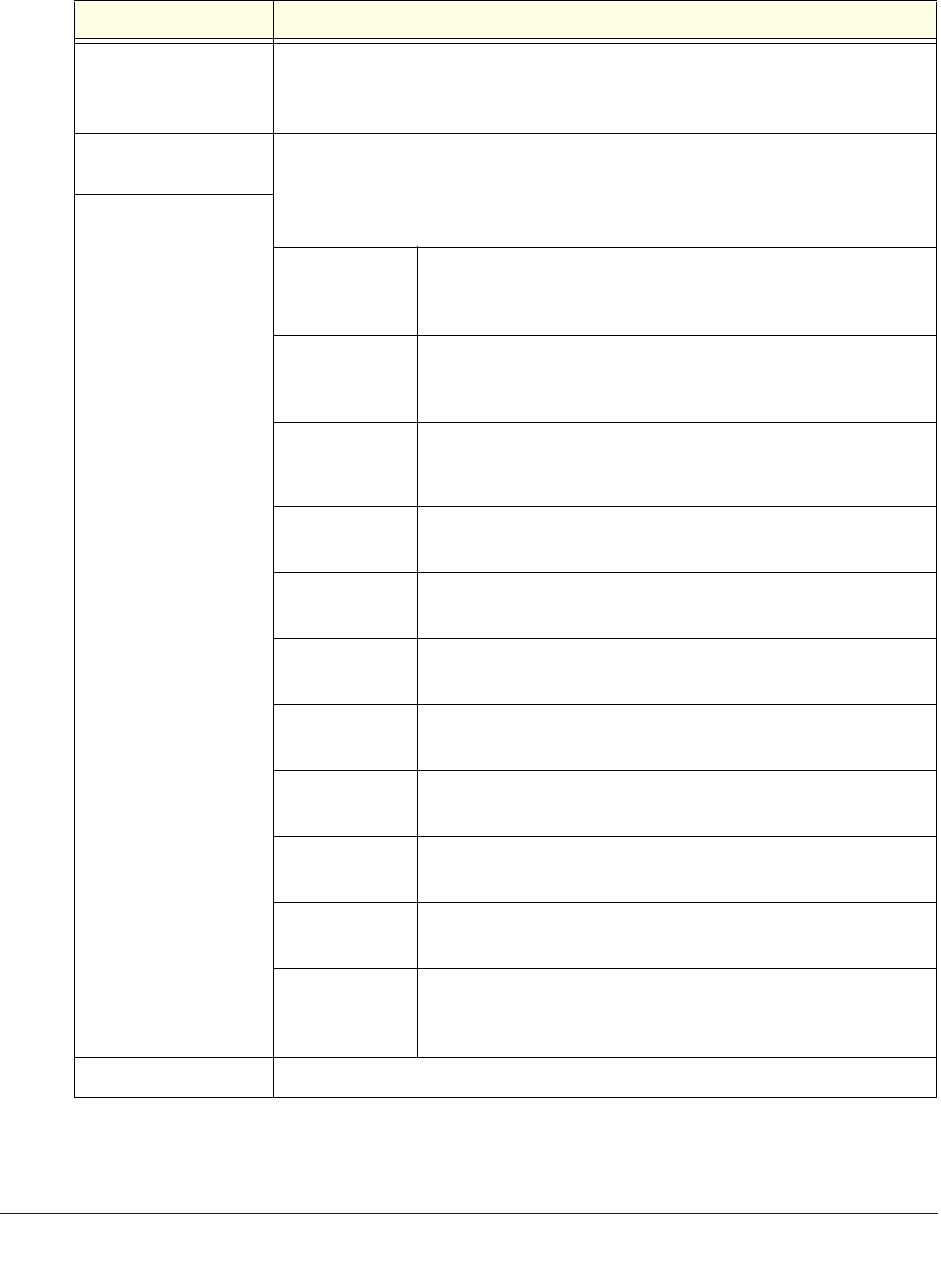
Table 135. Quarantine screen settings
Setting Description
File Type Select one of the following file types from the drop-down list:
• Spam. All intercepted spam.
• Malware. All intercepted viruses, spyware, and other malware threats.
View All Select one of the following radio buttons:
• View All. Display or download the entire selected log.
• Search Criteria. Query the selected log by configuring the search criteria that
are available for the selected log.
Search Criteria
Start Date/Time From the drop-down lists, select the year, month, day, hours,
and minutes for the start date and time.
This field is available for both the Spam and Malware logs.
End Date/Time From the drop-down lists, select the year, month, day, hours,
and minutes for the end date and time.
This field is available for both the Spam and Malware logs.
Protocols For the Malware log only, select one or more check boxes to
specify the protocols that are queried: SMTP, POP3, IMAP,
HTTP, FTP, and HTTPS.
Domain The domain name that is queried.
This field is available for both the Spam and Malware logs.
User The user name that is queried.
This field is available for both the Spam and Malware logs.
Malware Name The name of the malware threat that is queried.
This field is available only for the Malware log.
Client IP The client IP address that is queried.
This field is available for both the Spam and Malware logs.
Sender Email The sender’s email address that is queried.
This field is available only for the Spam log.
Recipient Email The recipient’s email address that is queried.
This field is available for both the Spam and Malware logs.
Subject The email subject line that is queried.
This field is available for both the Spam and Malware logs.
Size The minimum and maximum size (in bytes) of the file that is
queried.
This field is available for both the Spam and Malware logs.
Display The maximum number of pages that is displayed.


















